Please see the original post on IP Camera Security before reading the rest of this post.
Based on comment #2 by Carlo UART has been identified for my SRICAM AP001. Carlo stated that the board looks very similar to the NixCore and this is correct. I was not able to identify UART with JTAGulator because I never soldered any wires to pins 39 and 40!
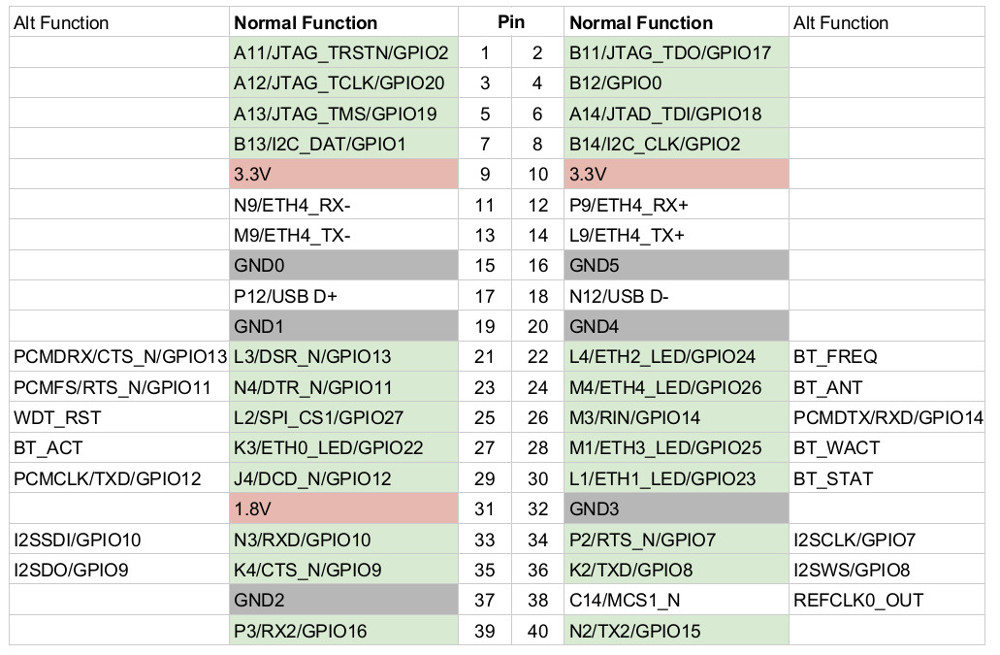
I soldered wires to RX2 (pin 39), TX2 (pin 40), and GND (pin 37) and connected them to a UART to USB adapter. Fired up minicom at 57600 8n1 and we have access!
U-Boot 1.1.3 (Dec 26 2012 - 17:31:39)
Board: Ralink APSoC DRAM: 32 MB
relocate_code Pointer at: 81fb4000
sysctl:40200300
spi_wait_nsec: 42
spi device id: ef 40 17 0 0 (40170000)
find flash: W25Q64BV
raspi_read: from:30000 len:1000
.raspi_read: from:30000 len:1000
.============================================
Ralink UBoot Version: 3.5.3.0
--------------------------------------------
ASIC 5350_MP (Port5<->None)
DRAM_CONF_FROM: Boot-Strapping
DRAM_TYPE: SDRAM
DRAM_SIZE: 256 Mbits
DRAM_WIDTH: 16 bits
DRAM_TOTAL_WIDTH: 16 bits
TOTAL_MEMORY_SIZE: 32 MBytes
Flash component: SPI Flash
Date:Dec 26 2012 Time:17:31:39
. . . SNIP . . .You can get the complete boot log here. Looking at /etc/passwd shows a DES encrypted hash where the plaintext is “123456”.
# cat /etc/passwd
root:LSiuY7pOmZG2s:0:0:Adminstrator:/:/bin/sh# In researching the NixCore I also came across a blog post from almost three (3) years ago the delves into an almost identical camera.
Looking at the PINOUT of the NixCore I’m going to see if this camera has JTAG enabled. BACK TO THE JTAGULATOR! Note that another site from the Google search of the unsalted hash shows that they were able to identify JTAG…but this board, while similar to the NixCore, is not the same as the AP001.
Okay I couldn’t wait and soldered up pins 1,2,3,5,6 and connected them to my BusBlaster v4 according to the NixCore documentation. No need for JTAGulator as the pinout was already documented.
So JTAG exists right when the device boots but then the GPIOs are reassigned. I assume to drive the motors to move the camera. I didn’t delve that far into it as i was only curious as to the existence of JTAG. The resources below include links to documentation on the Ralink RT5350 (datasheet) and configuration for OpenOCD. Maybe we can reach out to the creators of NixCore for an OpenOCD configuration file.
root@KALI:~# openocd -f /usr/share/openocd/scripts/interface/ftdi/dp_busblaster.cfg -c "adapter_khz 100; transport select jtag"
Open On-Chip Debugger 0.10.0+dev-00622-g322d2fa1 (2018-12-17-06:47)
Licensed under GNU GPL v2
For bug reports, read
http://openocd.org/doc/doxygen/bugs.html
Info : If you need SWD support, flash KT-Link buffer from https://github.com/bharrisau/busblaster
and use dp_busblaster_kt-link.cfg instead
adapter speed: 100 kHz
jtag
Info : Listening on port 6666 for tcl connections
Info : Listening on port 4444 for telnet connections
Info : clock speed 100 kHz
Warn : There are no enabled taps. AUTO PROBING MIGHT NOT WORK!!
Info : JTAG tap: auto0.tap tap/device found: 0x1535024f (mfg: 0x127 (MIPS Technologies), part: 0x5350, ver: 0x1)
Warn : AUTO auto0.tap - use "jtag newtap auto0 tap -irlen 5 -expected-id 0x1535024f"
Warn : gdb services need one or more targets definedResources
http://linuxgizmos.com/tiny-30-wifi-enabled-openwrt-module-runs-on-1-watt/
https://jelmertiete.com/2016/03/14/IoT-IP-camera-teardown-and-getting-root-password/
https://blog.tho.ms/hacks/2016/08/28/openwrt-on-logilink-wc0030a.html
https://www.pentestpartners.com/security-blog/hacking-the-ip-camera-part-1/
https://www.pentestpartners.com/security-blog/hacking-the-ip-camera-part-1/
http://liken.otsoa.net/blog/?x=entry:entry140322-183809
https://wikidevi.com/wiki/Ralink_RT5350
https://openwrt-devel.openwrt.narkive.com/e5kS1C19/openocd-and-rt3050-5350
http://www.jedge.com/docs/W25Q64BVSFIG-Winbond.pdf
http://www.jedge.com/docs/RT5350.pdf

