 Please see the original post on IP Camera Security before reading the rest of this post.
Please see the original post on IP Camera Security before reading the rest of this post.
Based on comment #1 by Carlo UART exists on his Hi3518 wifi cameras. He also mentions the default password of “zg2014” for both of his cameras. A Google search for that password reveals other Hi3518 cameras including the Mustcam H809P which has detailed images posted on a forum. This camera board is very different from the ESCAM QF100 but examining the traces from the SoC to the documented TX/RX on the Mustcam shows potential UART on the QF100. I was off by a couple pins based on my attempt in the original post.
The forum describing the Mustcam H809P has two HiRes images of the camera’s board (front and back). Examining and comparing the traces leading from the SoC on the H809P to the UART and the same traces on the QF100 shows that they lead under the MicroSD card reader. Before I removed the reader I examined the bottom of the QF100 board and saw a potential header. I soldered four wires and connected them to the JTAGulater. Using the JTAGulator is a bit overkill since you can easily identify GND via a continuity test and VCC with the same voltmeter. After that it is just swapping the other two options for RX and TX with your UART to USB adapter. But I do have a JTAGulator and it is simple to use.
. . . SNIP . . .
> v
Current target I/O voltage: Undefined
Enter new target I/O voltage (1.2 - 3.3, 0 for off): 3.3
New target I/O voltage set: 3.3
Ensure VADJ is NOT connected to target!
> u
. . . SNIP . . .
UART> u
UART pin naming is from the target's perspective.
Enter text string to output (prefix with \x for hex) [CR]:
Enter starting channel [0]:
Enter ending channel [2]:
Possible permutations: 6
. . . SNIP . . .
TXD: 0
RXD: 1
Baud: 115200
Data: ..Unknown comman [ 0D 0A 55 6E 6B 6E 6F 77 6E 20 63 6F 6D 6D 61 6E ]
------
UART scan complete.This images shows UART on the ESCAM QF100.
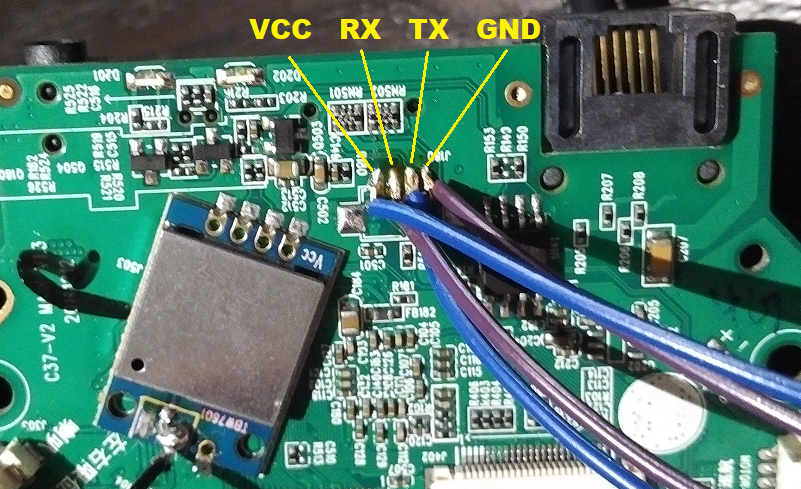
Connecting RX/TX/GND to your UART to USB adapter at 115200,8n1 and you have root access to the device.
U-Boot 2010.06 (May 17 2014 - 15:03:14)
Check spi flash controller v350... Found
Spi(cs1) ID: 0xC2 0x20 0x18 0xC2 0x20 0x18
Spi(cs1): Block:64KB Chip:16MB Name:"MX25L128XX"
In: serial
Out: serial
Err: serial
Hit any key to stop autoboot: 0
16384 KiB hi_sfc at 0:0 is now current device
## Booting kernel from Legacy Image at 82000000 ...
Image Name: Linux-3.0.8
Image Type: ARM Linux Kernel Image (uncompressed)
Data Size: 2134796 Bytes = 2 MiB
Load Address: 80008000
Entry Point: 80008000
Loading Kernel Image ... OK
OK
Starting kernel ...
Uncompressing Linux... done, booting the kernel.
Linux version 3.0.8 (root@ubuntu) (gcc version 4.4.1 (Hisilicon_v100(gcc4.4-290+uclibc_0.9.32.1+eabi+linuxpthread)) ) #30 Tue May 27 21:58:10 CST 2014
CPU: ARM926EJ-S [41069265] revision 5 (ARMv5TEJ), cr=00053177
CPU: VIVT data cache, VIVT instruction cache
Machine: hi3518
. . . SNIP . . .The full boot log can be found here. Examining the log shows that the device spits out the HTTP username and password in cleartext as well as the the WiFi ESSID and passphrase. NICE! Cracking the DES password hash for the root account found in /etc/passwd is “123456” just like so many of these devices.
Thank you Carlo for the hint!